I recently posted an article on how I used rsnapshot for backing up this blog. This worked fine but I was having two major issues with the approach.
1. Backing up the database’s internal file storage
Generally speaking, it’s bad practice to backup a database’s internal file storage as it could change mid-backup. A better approach would be to create a database dump which will result in a consistent snapshot.
2. Backing up volumes in archives
With the current approach of creating compressed tars of the Docker volumes, each time a full backup will be created. This uses up more space than necessary.
Borg to the rescue
Borg is an easy to use deduplicating archiver that comes with compression and encryption out of the box.
You can find a detailed manual and more info at https://www.borgbackup.org/.
Since I have to backup protected resources, I installed it with privileged access.
sudo apt update
sudo apt install borgbackupAt the time of writing this you may find the installation instructions under https://borgbackup.readthedocs.io/en/1.2.8/installation.html.
At this point we could go ahead and set up a (remote) repository and start backing up our data which would result in smaller backups than the previously used tar archives.
However, we still need a way to automatically backup the database as well as a convenient way to automate or backups.
Automate backups with Borgmatic
Borgmatic also comes with an exhaustive documentation that can be found at https://torsion.org/borgmatic/docs/how-to/set-up-backups/.
I’ve opted for a root install using apt.
sudo apt update
sudo apt install borgmaticNow that we have installed Borgmatic, let’s create a config file in /etc/borgmatic/config.yaml.
sudo borgmatic config generateNow, before editing the configuration file to our needs, let’s set up a remote repository with BorgBase first.
Remote backups with BorgBase
Sign up and receive 10 GB and 2 repositories for free forever. No credit card required. Just a place to keep your backups.
After setting up your free account it looks sth. like this.
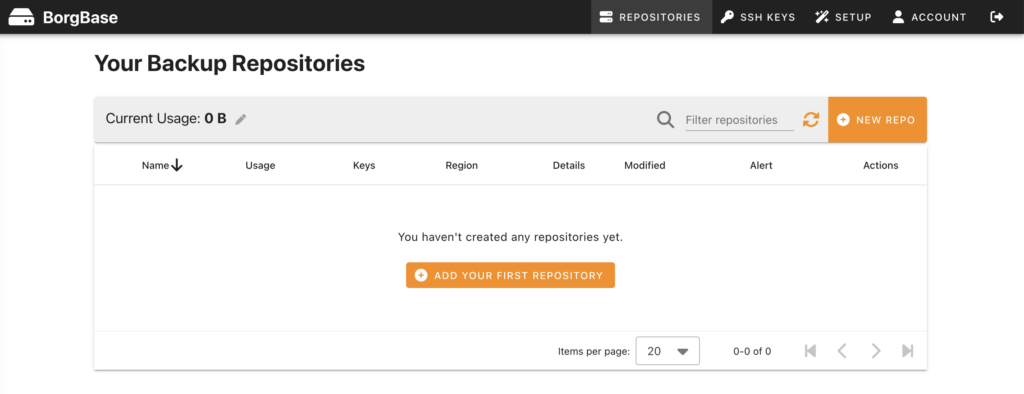
Before you may add a repository, you have to add a ssh key, first. BorgBase makes it very easy to add a key and guides you all the way. Here’s how I created my key.
ssh-keygen -t ed25519 -C "<EMAIL>" -f ~/.ssh/id_ed25519_borgbasePlease replace <EMAIL> with your own mail address. The above will generate a new key and place it under .ssh in your home folder under the name of id_ed25519_borgbase. In addition it will generate a corresponding public key. This is what you must provide BorgBase with in order to create and access a repository. Type the following to access it from your terminal:
cat ~/.ssh/id_ed25519_borgbase.pubAfter setting up your repository you will be presented with a wizard to set up your server for communicating with it.
Now it’s time to edit the borgmatic config file from earlier. It’s pretty self explanitory.
I’m including everything under /etc, my home folder as well as the Docker volume for this blog.
source_directories:
- /etc
- /home/<USER>
- /var/lib/docker/volumes/<VOLUME_NAME>There is a detailed explanation on how to include database dumps in your backups available at https://torsion.org/borgmatic/docs/how-to/backup-your-databases/.
I added the following snippet to my config.
mariadb_databases:
- name: <DB_NAME>
hostname: 127.0.0.1
port: 3306
username: <USER>
password: <PASSWORD>After your done, you may validate your config with the following command.
sudo borgmatic config validateThe last thing to do is initializing the repository.
sudo borgmatic init --encryption repokeyTest your setup
Before editing your crontab, it makes sense to test your setup manually.
sudo borgmatic create --verbosity 1 --list --statsIf everything works as expected, you should add a call to borgmatic to the root user’s crontab.
sudo crontab -eConclusion
And now you can lie back and relax. Depending on your crontab settings your incremental backups will be created automatically and will be securely encrypted stored off site.
Nice!
Leave a Reply